Managing Test Credential
Overview:
Credentials are critical data used during testing. They are crucial not only for the test outcomes but also demand high levels of security and confidentiality. The Testany Platform’s Testany Secrets Service (TSS) ensures end-to-end protection of credentials throughout the testing process, preventing their leakage during storage, retrieval, and execution.
Understanding Testany Secrets Service
TSS definition: (Aka TSS) Testany Secrets Service is a specialized service designed to fetch secrets from Trusted Certificate Safes, such as Azure Key Vault and AWS Secrets Manager. It facilitates secure retrieval of sensitive information like keys and certificates, ensuring data security and compliance with industry standards. The service operates by receiving requests to extract specific secrets identified by keys and responds with the requested data, thus playing a crucial role in secure information management. ( <Glossary> )
In the Testany Platform design, TSS is integrated with the Test Execution Runtime module in a one-to-many relationship. The management of test credentials varies depending on the deployment method of the runtime, whether it is Testany Managed Cloud or Self-Managed Cloud.
If you have some secure data like credentials which need to be used in your test case, you can use Testany Secrets Service to enable tests retrieve credential/secure data via Credential Safe during execution.
Manage Credential Safe
This document is intended primarily for Workspace Admins responsible for managing test credentials. Other roles may also find it useful for reference.
Understanding the concept of “Credential Safe”
In the design of the Testany Platform, all credentials used in testing themselves must and can only be stored in a safety place provided by third-party services that comply with all relevant information security laws and regulations. These third-party services could be IaaS or SaaS providers.
Currently, the Credential Store integrated with Testany Secrets Service include:
AWS Secrets Manager
Azure Key Vault
To ensure that running test programs can securely and automatically read credentials stored in third-party credential stores during automated test execution, and to prevent credential leakage throughout the entire test lifecycle, users need to use Testany Secrets Service to establish an association between the test scripts and these credentials. For detailed steps, refer to Managing Test Case (testany.io).
Thus, a “Credential Safe” is a virtual object representing a third-party credential store on Testany Platform, and a “Credential” is also a virtual object representing the credentials stored in that credential store.
Create Credential Safe
Before you start…
Ensure you have Admin privileges for the Workspace where you need to create the Credential Safe.
Create access permissions for TSS to access the third-party Credential Store corresponding to the Credential Safe that will be created (either via username and password or IAM method).
Step-by-Step Guide
Click Workspace settings
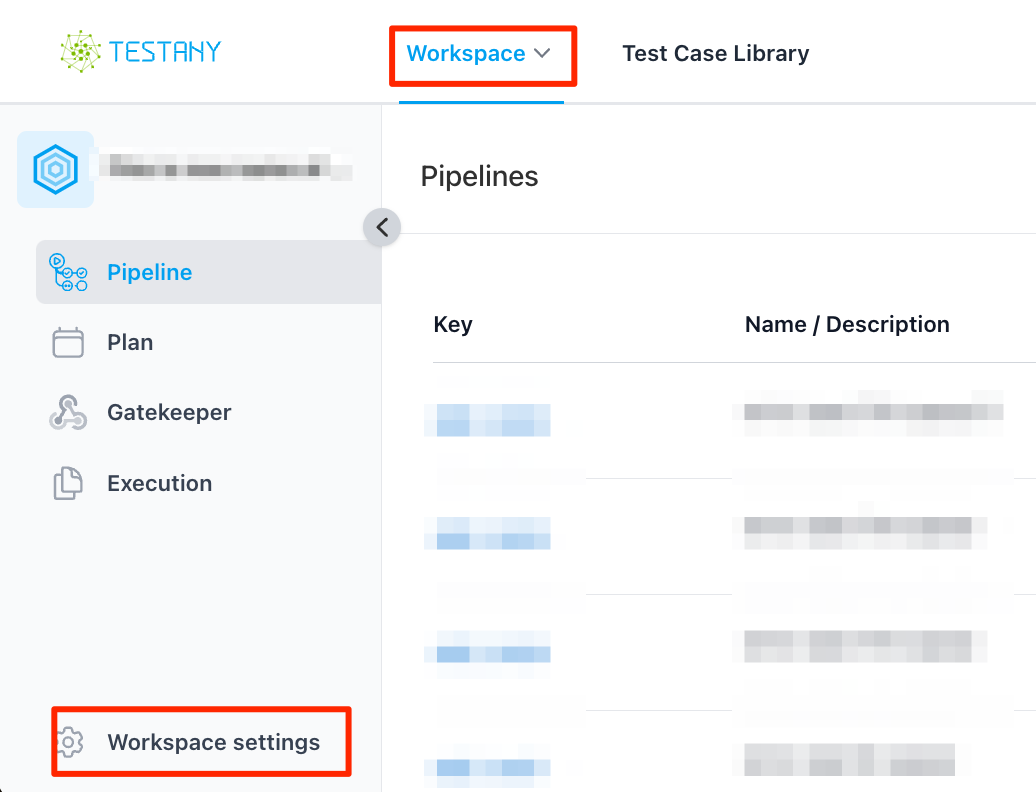
Navigate to Credential tab and select the Runtime that needs to be associated with the Credential Safe to be created
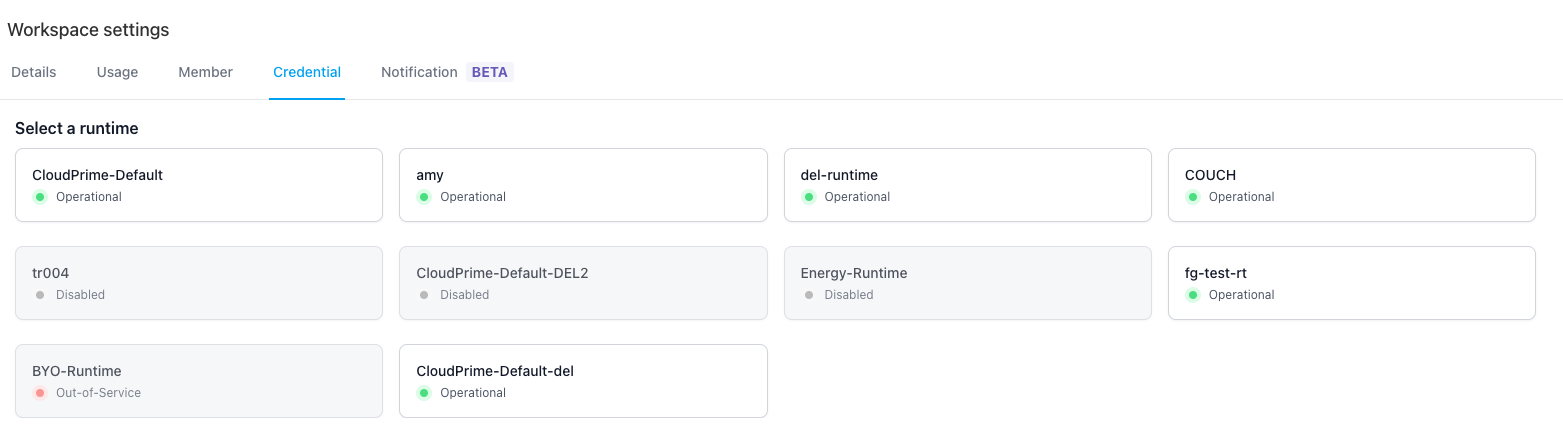
click “Add credential safe” button
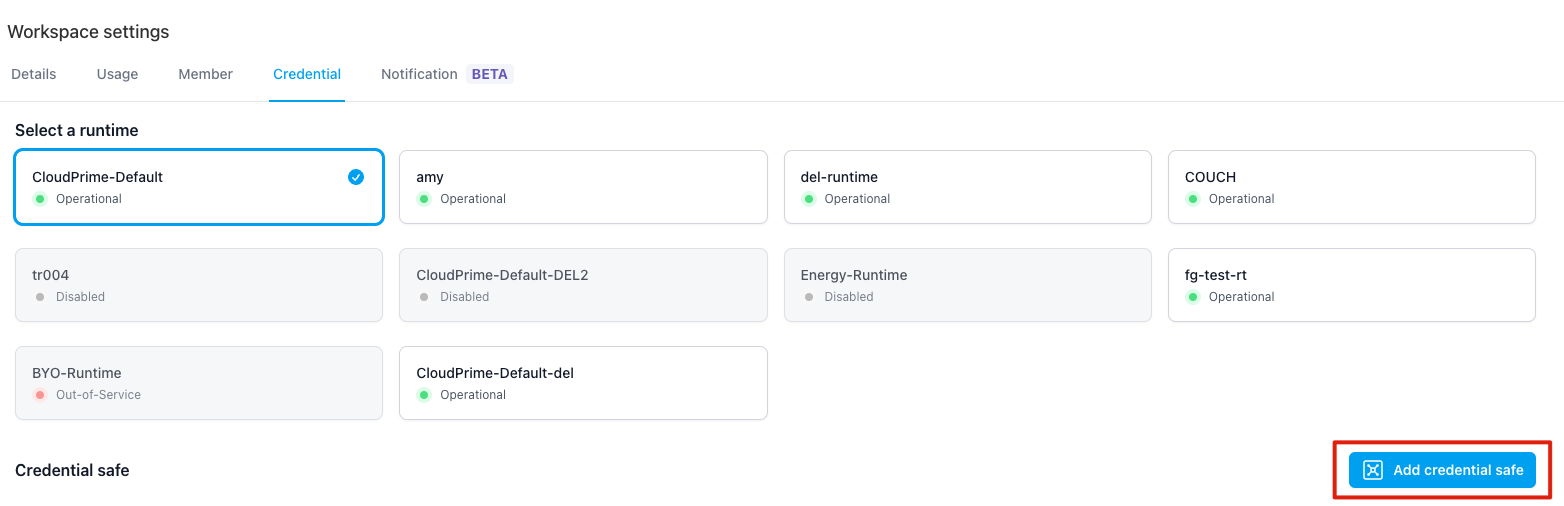
- If the Runtime you’ve selected is “CloudPrime-Default”
Provide related information then click “Submit” button
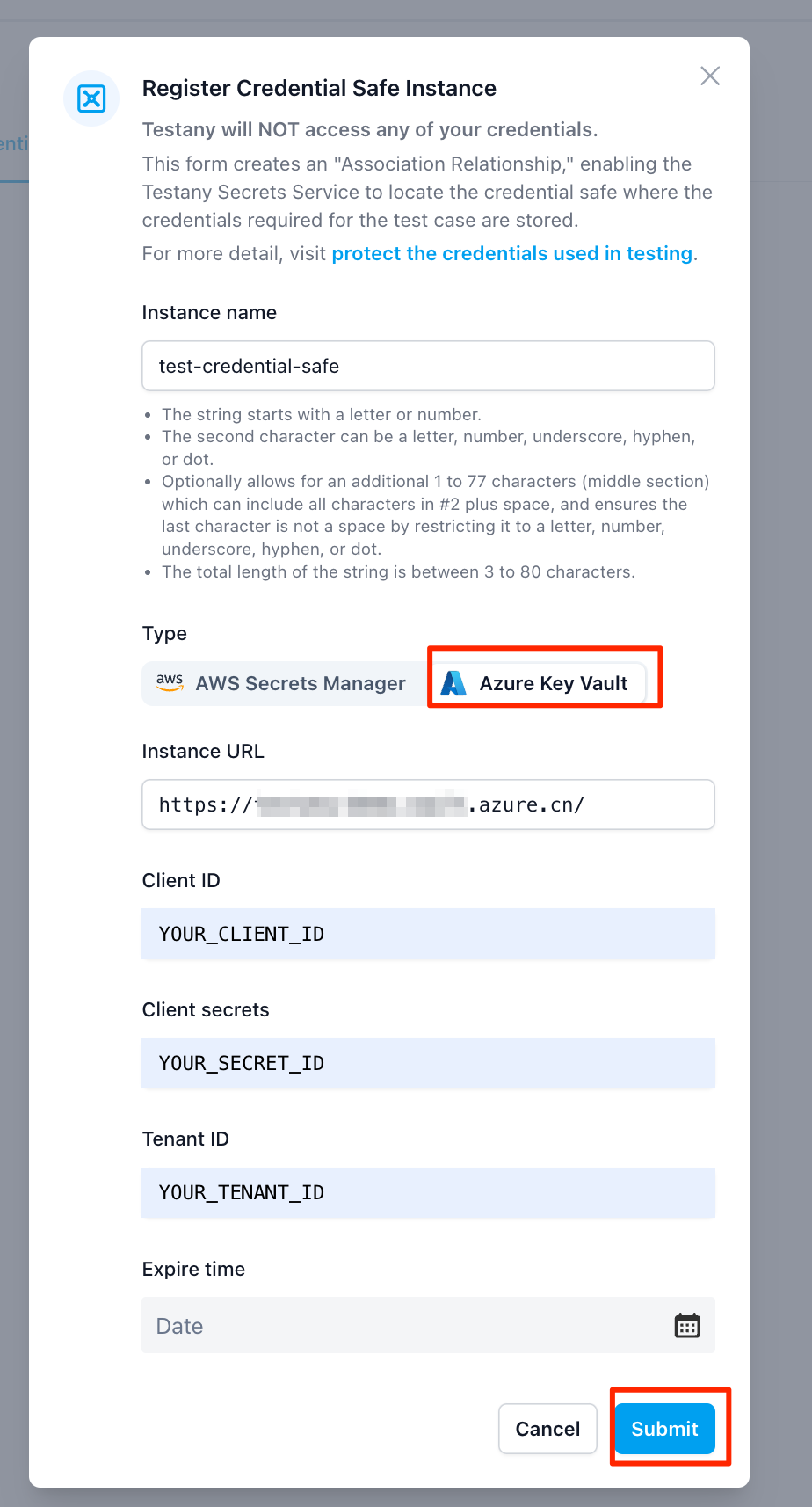
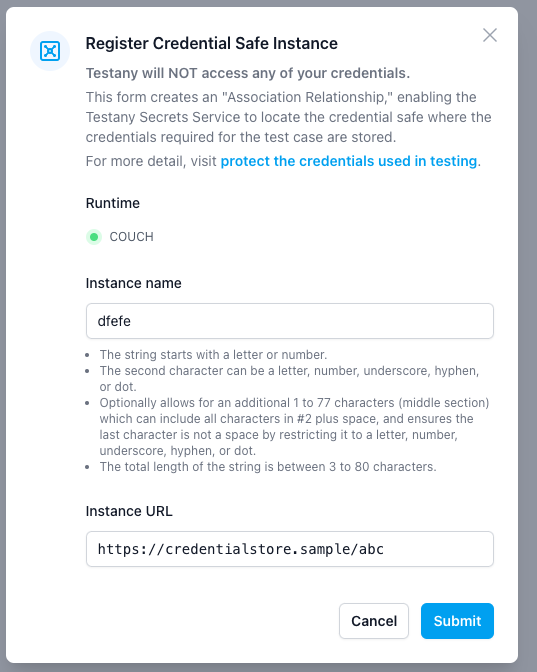
- If the Runtime you selected is NOT “CloudPrime-Default”
You’ll be asked to provide the Credential Safe instance name and URL
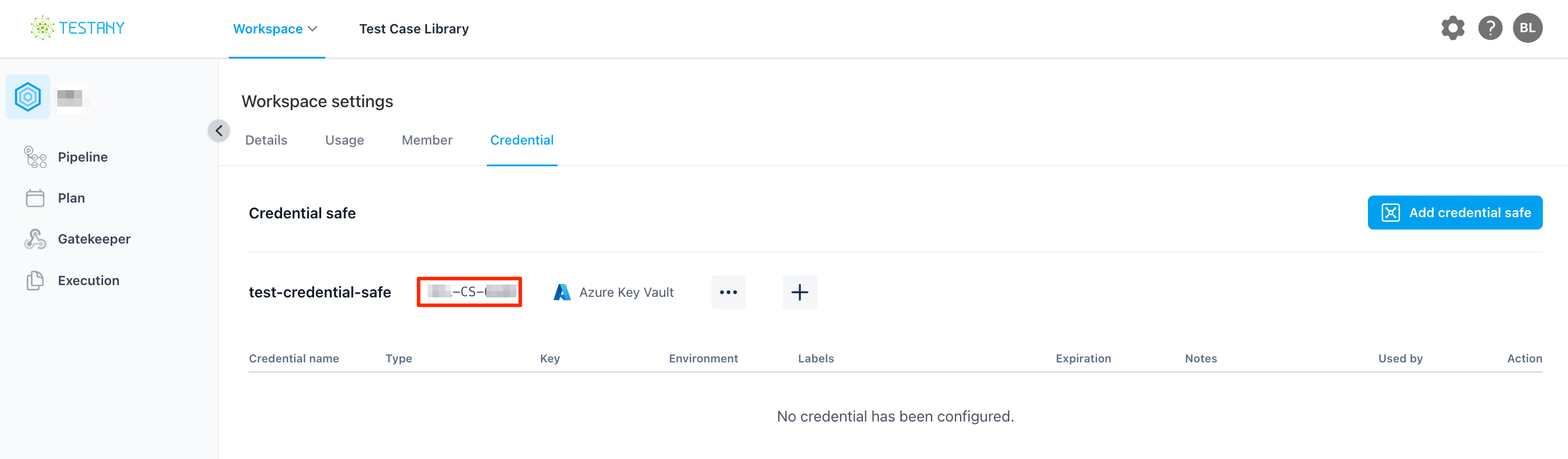
After the creation, you will get a credential safe key, the key will used for identity which Credential Safe you want to use. It will be used in your code.
Edit Credential Safe
You may edit the name and URL of the existing Credential Safe by click here:
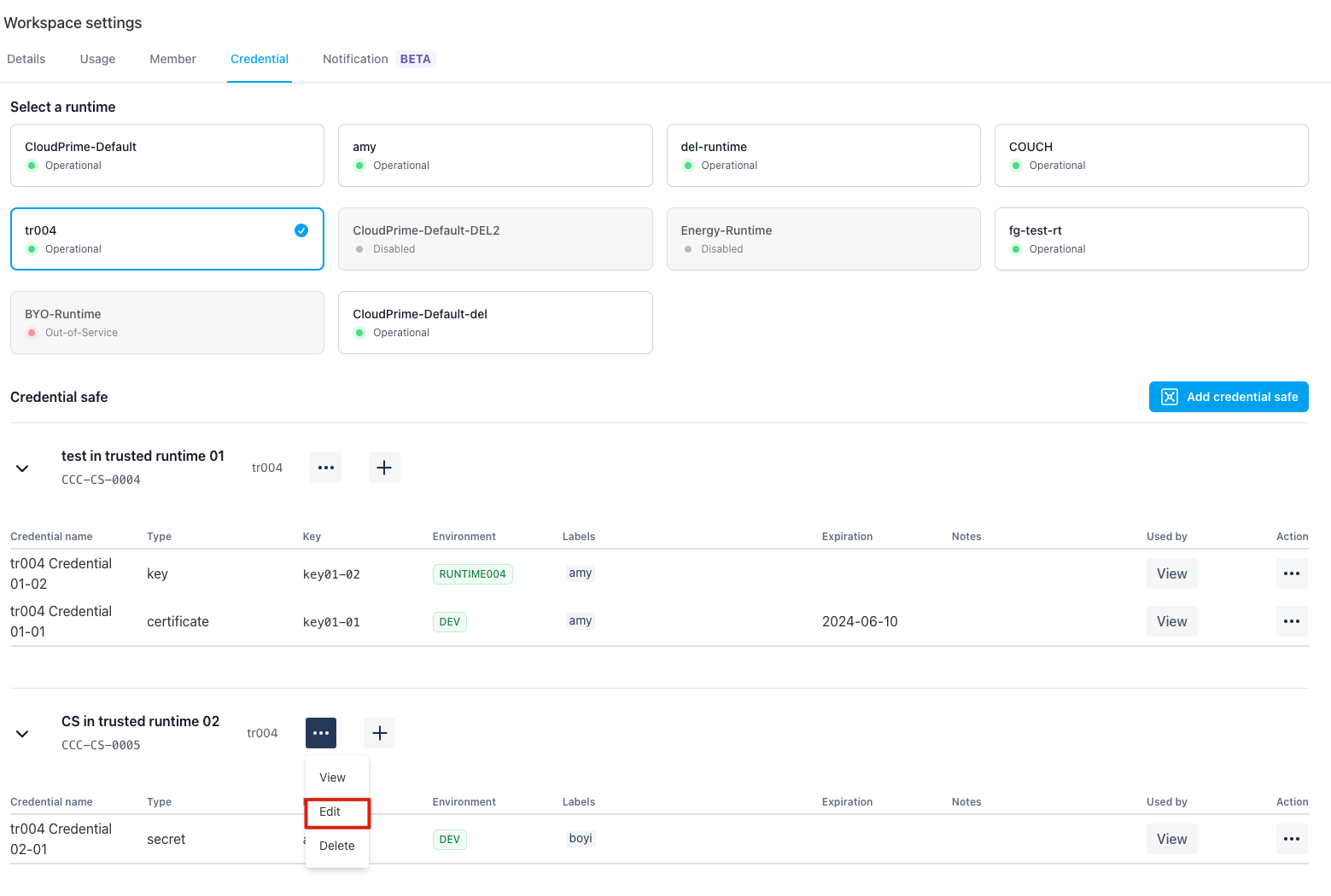
Please note the Credential Safe key is NOT allowed to be edit.
Delete Credential Safe
You may delete an existing Credential Safe by click here:
Credential which are created under the Credential Safe will be deleted too if you delete a Credential Safe. And all tests which reference the credentials will be immediately impacted.
Manage Credential Key under Credential Safe
The credential key is the key name for your credential which stored in your managed Credential Safe
You need provide the key name under one credential safe, then you could bind this credential to multiple test cases
Add credential in your credential store (Azure Key Vault or AWS Secrets Manager)
In Azure Key Vault, the credential create command. More details about Azure Key Vault
az keyvalult secret set --vault-name <YOUR-VAULT-NAME> --name client-secret --value <YOUR-SECRET-VALUE>In AWS Secrets Manager, the credential stored like this(
client-secret). More details about AWS Secrets Manager
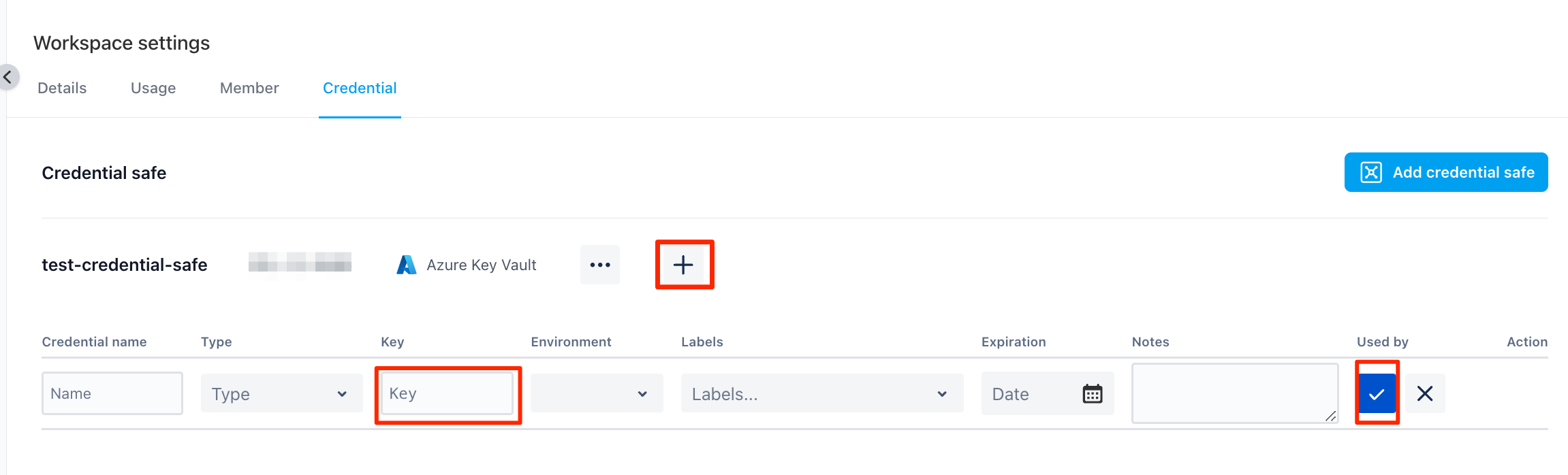
Add Credential Key on Testany Platform
Click “+” to add the key name you will create in your Credential Safe.
Credential name, it is a display name for the credential key nameType, it is the credential type(key/secret/certificate)Key, it is the credential key name. it MUST be same as the Key (client-secret) your created in the step of “Add credential in your credential store”.
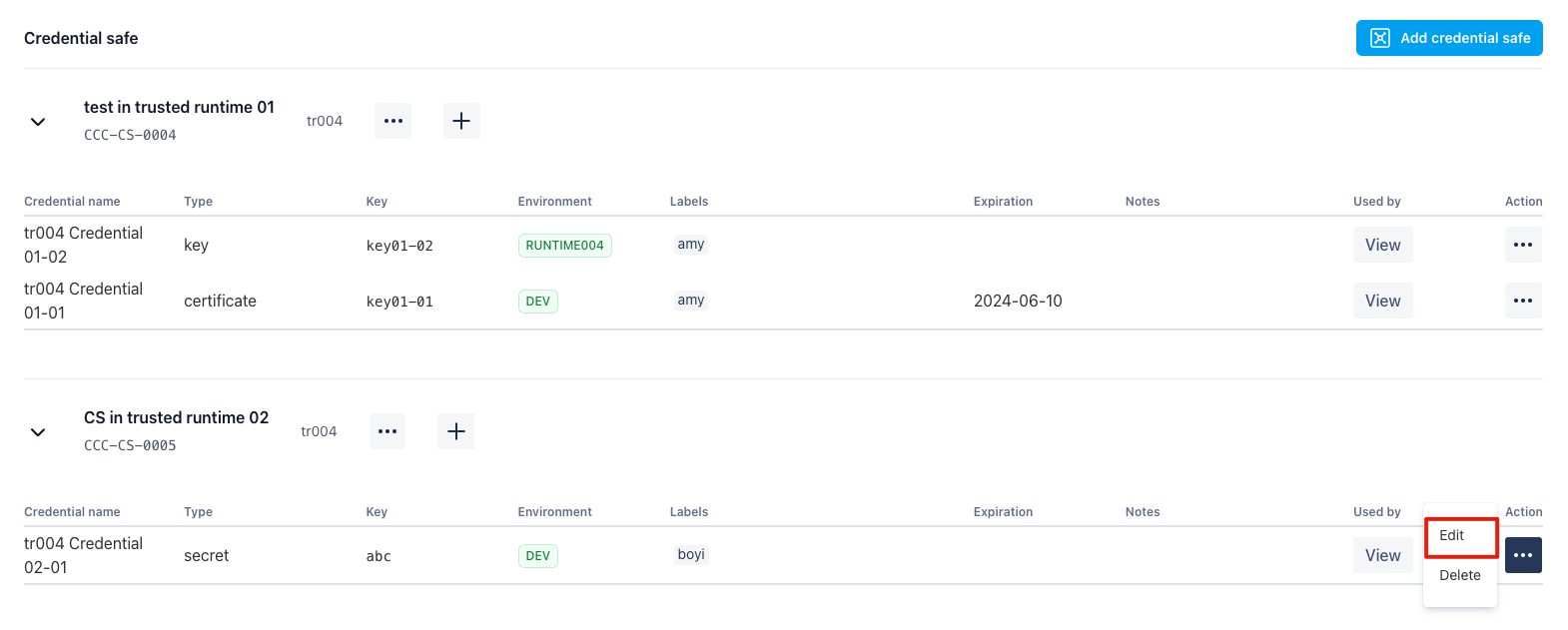
Edit Credential Key
By click the “edit” button, you may edit the credential key information:
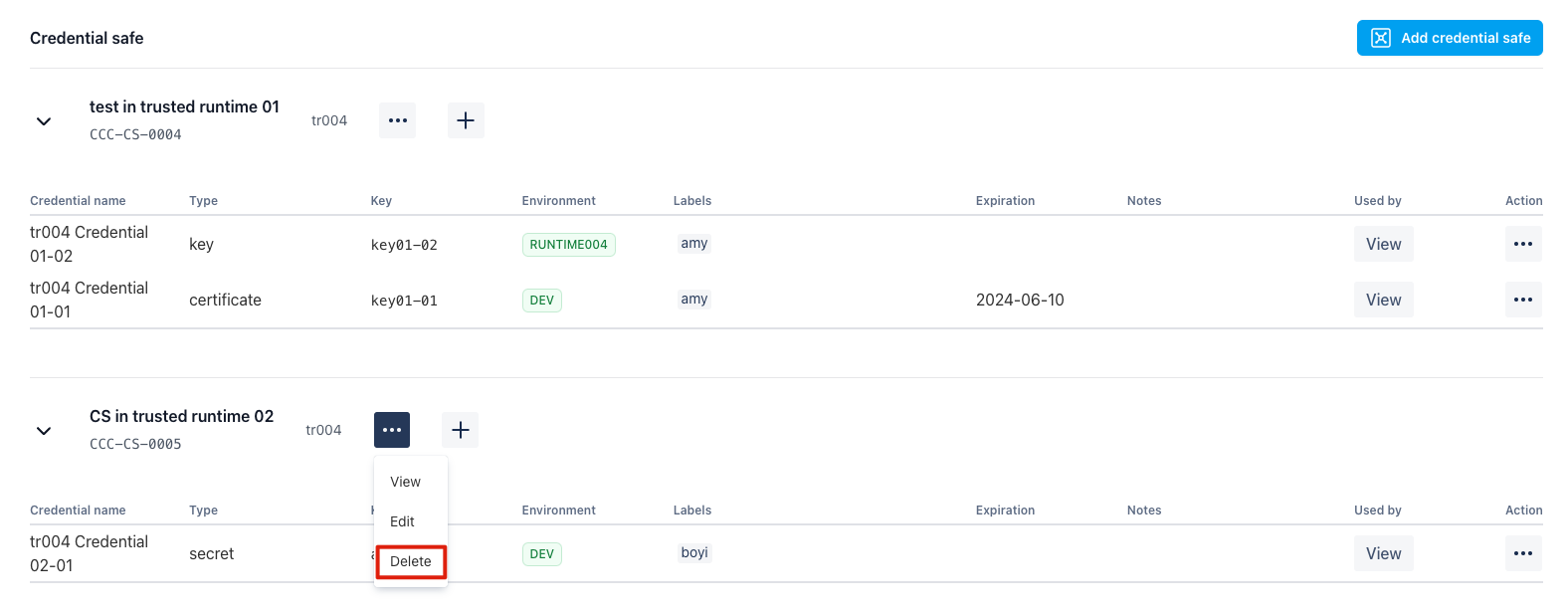
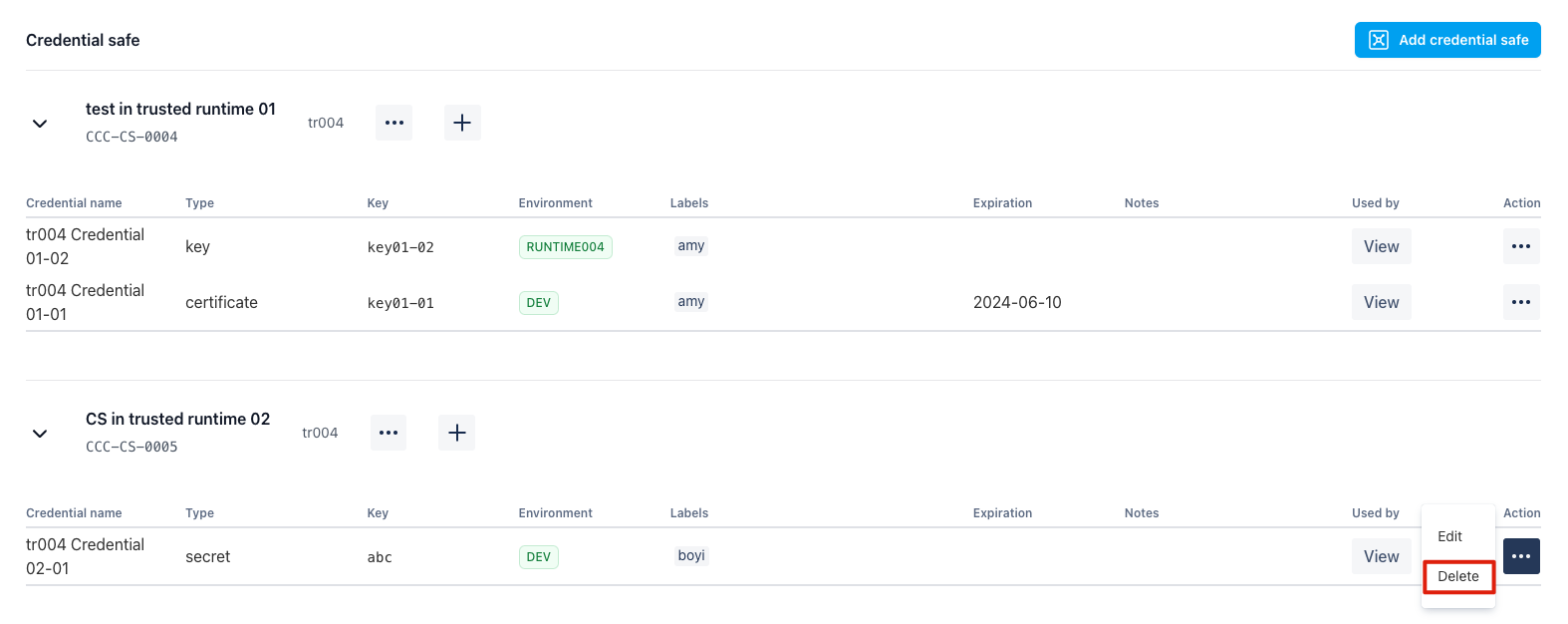
Delete Credential Key
By click the “delete” button, you may delete the credential key you’ve picked. Please note the test cases which has referenced this Credential Key will be impacted immediately.
Reference Credential in test case
To reference a Credential in your test cases, you need to ensure that both the Testany Platform and your test code are aware of the Credential you are using. Therefore, you need to configure it in two places:
On the Testany Platform
In your test code
Config on the Testany Platform
Bind credentials to specific Test cases
Go to test case detail page, click edit
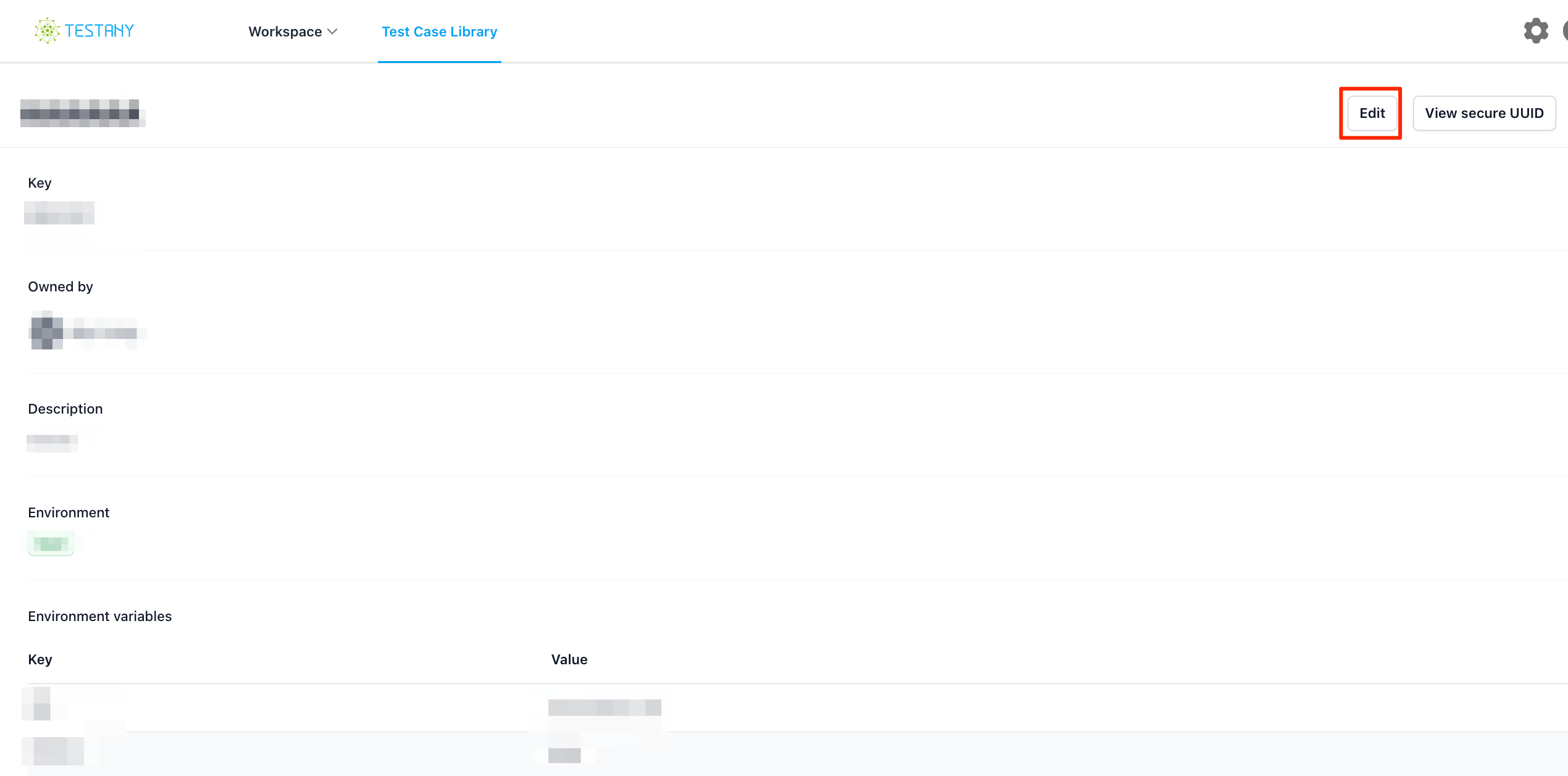
click “Add a new secure key reference“, and choose the Workspace, Safe and Credential
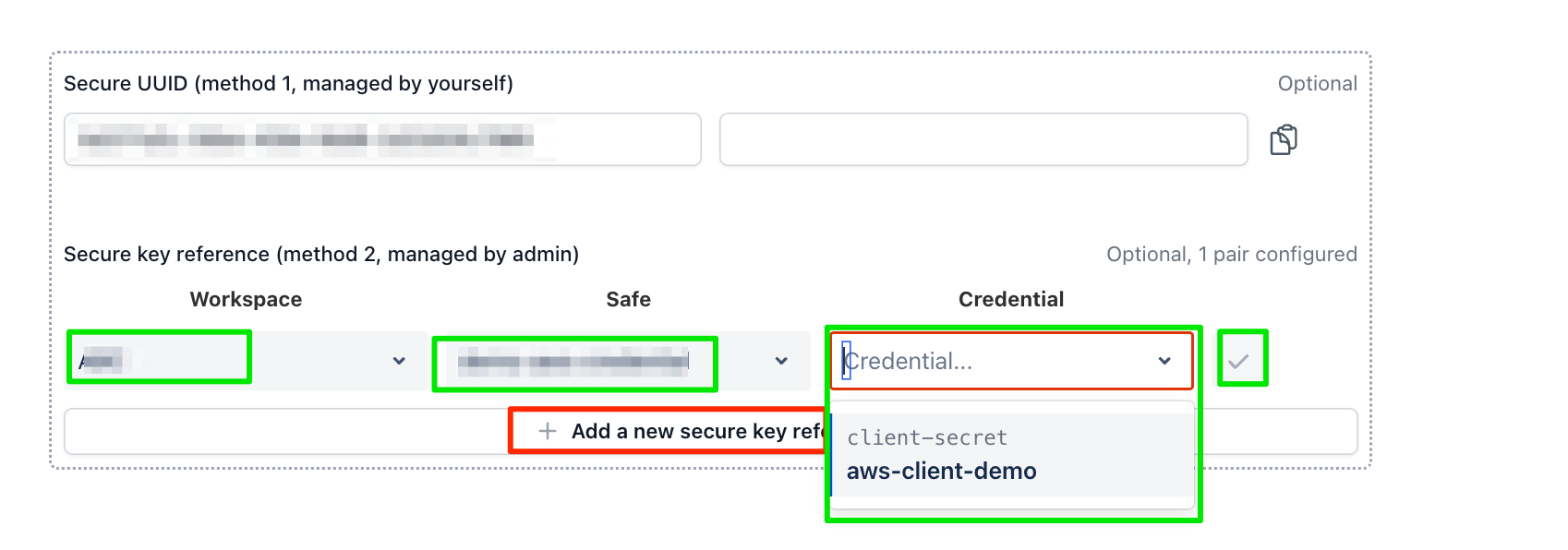
Click button “Save”, then the credential client-secret will bind to this test case.
Add code to your test script
In your test case, you can use Environment TESTANY_SECRETS_SERVICE to get the TSS(Testany Secrets Service) URL, and add the key as the parameter in your URL.
Supported parameters:
key: Your secrets key name which stored in your Credential Safe. DO NOT provide the
secureUUID in it.safe_key: “safe_key” indicates a particular Key Vault instance that you can use. The workspace Admin created in Step Create Credential Safe.
TSS API more details see the swagger file below:
openapi: 3.0.3
info:
title: Swagger Testany Secrets Service
description: |-
Testany Secrets Service API.
### Check out its awesome features:
* Retrieve secrets
* Retrieve certificates
* Retrieve keys
termsOfService: http://swagger.io/terms/
contact:
email: support@testany.io
license:
name: Testany
url: https://www.testany.com.cn
version: 2.0.0
servers:
- url: TESTANY_SECRETS_SERVICE
tags:
- name: Testany Secrets Service
description: Fetch Secrets
paths:
/:
get:
tags:
- Testany Secrets Service
summary: Fetch secrets from Trusted Certificate Safe
description: Fetch secrets from Trusted Certificate Safe, like Azure Key Vault, AWS Secrets Manager
operationId: retrieveSecrets
parameters:
- name: key
in: query
description: |
The key name in your Trusted Certificate Safe(TCS), like Azure KeyVault, AWS Secrets Manager etc. Please DO NOT provide the SecureUUID in this parameter. The key you **stored** in TCS is `<SecureUUID>-<key_name>`, this parameter should **ONLY** `<key_name>`, Testany will auto ingest the SecureUUID when retrieve secrets from TCS.
If the key name is used for multiple cases, the key need to be created under the credential safe which created by Workspace Admin. And the key need to bind to the case.
required: true
schema:
type: string
# - name: key_type
# deprecated: true
# in: query
# description: Default is **secrets** if not provide this parameter
# required: false
# schema:
# type: string
# enum:
# - secrets
# - keys
# - certificates
- name: group
deprecated: true
in: query
description: |
The group parameter is only used for TSS V1
Currently the group name configured by Testany. If you need use your specific Trusted Certificate Safe, like a new Azure Key Vault URL, please contact Testany Support Team. In the further, the group will be configured by your workspace admin.
required: true
schema:
type: string
- name: safe_key
in: query
description: |
Currently the safe_key name created by Workspace Admin. If you need use your specific Trusted Certificate Safe, like a new Azure Key Vault URL, please contact your Workspace Admin.
required: true
schema:
type: string
responses:
'200':
description: successful operation
content:
application/json:
schema:
type: object
properties:
value:
type: string
description: |
Depends on what value you stored in your Trusted Certificates Safe
'400':
description: Invalid key type value
components:
schemas:
keys:
description: |
if key_type is keys, the response string is a json format string
properties:
key:
type: object
properties:
kid:
type: string
kty:
type: string
key_ops:
type: array
items:
type: string
n:
type: string
e:
type: string
attributes:
type: object
properties:
enabled:
type: string
created:
type: integer
example: 161010101
updated:
type: integer
example: 161010101
recoveryLevel:
type: string
certificates:
description: |
if key_type is certificates, the response string is a certificate pem string
example: |
-----BEGIN CERTIFICATE-----\nMIIDPDCCxxxxxxxxxxxxxxsFADAb\nMRkwFwxxxxxxxxxxxNDMwNloXDTI0\nMDkxMTA3NxxxxxxxxxxxxxDQYJ\nKoZIhxxxxxxxxxxxI0sldgU\nxxxxxxxxxxxlsqMK\n3hpTxxxxxxxxxqou3b\nFanxxxxxxxxxxxxxNqhh\nOMuEfjK7kvGxxxxxxxxxWRvCteW\natxxxxxxxxxxxxxxxwEAAaN8\nMHoxxxxxxxxxxxxxxxxxxBQUH\nAwExxxxxxxxxMB0G\nA1UdDgxxxxxxxxxxEA\nVgsjWlIxxxxxxxxA2EF\nS5vwLExxxxxxxxxYTUE\n/2ZQW+j+icoxxxxxxxxxNeh4g\nljtBpX4ugxxxxxxxmnS9jb\nSZxxxxxxxxxx0yFLOyiF5W2Yp\nk+JWxxxxxxxx7AiA==\n-----END CERTIFICATE-----\nSample code
Here is a Postman example, you can send a GET request in Postman Pre-request Script to retrieve your specific credential.
const postRequest = {
url: pm.environment.get("TESTANY_SECRETS_SERVICE")+'?key=client-secret&safe_key=XXX-CS-XXXX',
method: 'GET',
header: {
'Content-Type': 'application/json'
}
};
pm.sendRequest(postRequest, (error, response) => {
if(error){
console.log(error)
}
pm.test("Retrieve Secrets is OK", ()=> {
try{
pm.expect(error).to.equal(null);
pm.expect(response).to.have.property('code', 200);
pm.expect(response).to.have.property('status', 'OK');
pm.expect(response.json()).to.not.have.property('error')
var secret_value = JSON.parse(response.json()['value'])
pm.environment.set("my-secret", secret_value)
}catch(e) {
console.log(response.json())
throw new Error("Retrieve Secrets Error ["+ e.message +"]")
}
})
});curl command
curl -X GET ${TESTANY_SECRETS_SERVICE}?key=client-secret&safe_key=XXX-CS-XXXXAttached test case with credentials example: postman-with-credential.zip